By: Andrew Childers and Simrun Mithwani
Babies born “preterm” is defined as being born alive before 37 weeks of pregnancy are completed. Per the Centers for Disease Control and Prevention (“CDC”), preterm birth occurs in more than 10% of infants born in the United States. Those preterm infants are typically transferred to a Neonatal Intensive Care Unit (NICU) immediately after being born and remain in the NICU until such time as their bodies have developed to a point that they can survive without the high level of care provided by a NICU. An important part of caring for preterm babies is providing them with sufficient nutrition to ensure they grow appropriately.Necrotizing Enterocolitis (“NEC”) is a potentially deadly intestinal disease suffered primarily by preterm infants, that is characterized by inflammation and injury of the gut wall barrier that may advance to necrosis and perforation of the gut. Advanced cases of NEC often lead to surgery and even death. The rate of NEC in preterm infants fed cow’s milk-based nutrition products is exponentially higher than in preterm infants fed an exclusively human milk-based diet.
Preterm infants who have ingested cow’s milk-based formulas or fortifiers are particularly susceptible to NEC because, as preemies, they do not have fully developed digestive systems, which makes them even more vulnerable to damage from bacteria found in cow’s milk-based formulas. The risk of NEC is dramatically increased in preterm infants who are fed cow’s milk-based formulas as opposed to a human milk-only diet, as they are 4.2 times more likely to get NEC and they are 5.1 more times likely to require surgery or die as a result of NEC. Replacing cow’s milk-based products with human milk or human milk-based products is the most effective intervention for preventing NEC in preterm infants.
The American Academy of Pediatrics has repeatedly espoused that human donor milk is the best feeding option for premature infants whose mothers are unable to produce enough of their own milk (“mother’s own milk” or “MOM”) to keep up with their babies’ nutritional needs. Human donor milk can be obtained from human milk banks, which are widespread across the United States. At least 31 human milk banks are currently members of the Human Milk Banking Association of North America, which ensures donor milk is pasteurized and lab-tested to eliminate contamination. If an individual is unable to obtain human donor milk, alternative human milk-based products, which are further described in the Reasonable Alternative Design section below, have been available in the United States since 2006.
 Abbott Laboratories (“Abbott”) designs, manufactures and sells cow’s milk-based preterm infant nutrition products under the Similac® brand name. Mead Johnson & Company, LLC (“Mead Johnson”) designs, manufactures and sells cow’s milk-based preterm infant nutrition products under the Enfamil® brand name. Similac® and Enfamil® are by far the most common cow’s milk-based food products fed to premature infants in NICUs in the United States and, because of their similarity they are, are often used interchangeably by NICU staff.
Abbott Laboratories (“Abbott”) designs, manufactures and sells cow’s milk-based preterm infant nutrition products under the Similac® brand name. Mead Johnson & Company, LLC (“Mead Johnson”) designs, manufactures and sells cow’s milk-based preterm infant nutrition products under the Enfamil® brand name. Similac® and Enfamil® are by far the most common cow’s milk-based food products fed to premature infants in NICUs in the United States and, because of their similarity they are, are often used interchangeably by NICU staff.
Abbott’s and Mead Johnson’s marketing of their cow’s milk-based products includes targeting parents of preterm infants while they are still in the hospital with the message that cow’s milk-based formulas and fortifiers are necessary for the growth and development of their vulnerable children. These tactics implicitly discourage mothers from breastfeeding, which reduces the mother’s supply of breast milk. None of Abbott’s or Mead Johnson’s marketing materials, including their promotional websites, reference the science showing how significantly their products increase the risk of NEC.
Numerous studies have shown the detrimental impact of formula advertising on the rates of breastfeeding, including studies that show that when the number of such advertisements increases, reported breastfeeding rates decrease in the following year. Abbott and Mead Johnson are aware that their advertising efforts disincentivize breastfeeding and incentivize the use of formula, which boosts their profits. Abbott and Mead Johnson, along with other formula manufacturers, spend tremendous sums of money to continue such advertising. In 2014 alone, formula manufacturers spent $4.48 billion on marketing.
In 1981, the World Health Assembly, the decision-making entity for the World Health Organization (“WHO”), recognized the abuse and dangers of infant formula marketing and developed the International Code of Marketing of Breast-milk Substitutes (“International Code”), which required companies to acknowledge the superiority of breast milk, the negative effect of introducing partial bottle-feeding on breastfeeding and the difficulty of reversing the decision not to breastfeed. The International Code also forbade advertising or other forms of promotion of formula to the general public, including providing sample products to mothers or members of their families.
Although Abbott and Mead Johnson acknowledge the International Code on their websites and claim to support the effort to encourage mothers to breastfeed for as long as possible, their aggressive marketing aims to convince parents of premature infants that an exclusive human milk-based diet will not provide their baby the best chance of survival And the companies do so while failing to warn those same parents that their products come with a significantly increased risk of NEC.

For example, Abbott’s website, on a page titled “Infant Formula Marketing” states: “We agree with the World Health Organization that breastfeeding provides the best nutrition for babies, and we support its goal to increase breastfeeding. We also recognize that for infants who aren’t breastfed—for medical reasons or otherwise—infant formula is the only appropriate, safe alternative to meet babies’ nutritional needs.” This statement completely ignores the existence of donor milk and human milk-based formula products and the science showing that an exclusive human milk-based diet is sufficient to allow a preterm infant to thrive.
In advertising its preterm infant nutrition products, Abbott emphasizes the products’ purported ability to assist underdeveloped babies in reaching their growth targets. For example, on the since-edited webpage regarding Similac NeoSure, Abbott noted: “Your premature baby didn’t get her full nine months in the womb, so her body is working hard to catch up. During her first full year, feed her Similac NeoSure, a nutrient-enriched formula for babies who were born prematurely and help support her development.” Abbott’s website made no mention, however, of the exponentially increased risk of NEC NeoSure causes.
In advertising its preterm infant nutrition products, Mead Johnson emphasizes the purported similarities between its formula and breast milk while failing to include any information about the nutritional deficits and dangers that accompany formula use. For example, the since-edited webpage for Enfamil Enfacare stated: “Premature babies fed Enfamil® formulas during the first year have achieved catch-up growth similar to that of full-term, breastfed infants” and “Includes expert-recommended levels of DHA and ARA (important fatty acids found naturally in breast milk) to support brain and eye development.” One Enfamil advertisement, introducing a new product line called Enfamil NeuroPro is entirely focused on favorably comparing Enfamil’s formula to breast milk, without any mention of the product’s extreme risks. Indeed, the terms “human milk” and “breast milk” are used 13 times in the advertisement, including in such statements as “for decades human milk has inspired the advancement in Enfamil formulas and now, through extensive global research, we are taking an even closer look at human milk” and “only Enfamil NeuroPro has a fat blend of MFGM and DHA previously found only in breast milk.” The webpage for the product has made similar manipulative claims stating, “Enfamil is backed by decades of breast milk research and multiple clinical studies” and claiming that “to create our best formulas, we collaborated on some of the most extensive breast milk studies to date.”
Like Abbott, Mead Johnson recognizes that many countries have adopted the International Code as law and states on its website, on a page titled “Terms of Use”: “Mead Johnson Nutrition endorses the aim of the World Health Organization (WHO) International Code of Marketing of Breast-milk Substitutes in developing countries, including standards for product integrity, labeling, distribution and promotion. Mead quotes from the International Code that “breastfeeding is best for infants,” but then contradicts the WHO by stating that “Formula, when used properly, provides a sound nutritious substitute or supplement to breast milk, but it is more expensive”.
In addition to their aggressive direct-to-consumer marketing, for decades Abbott and Mead Jonson have used their relationships with hospitals to encourage parents to substitute formula for breast milk after mothers and their babies are discharged from the hospital, offering free formula, coupons and even entire gift baskets to parents in hospitals, medical clinics and residential charities where out-of-town families stay while their babies receive long-term treatment in the NICU. Abbott and Mead Johnson seek to create brand loyalty in hopes that new parents will continue to use their Similac® or Enfamil® formulas after they leave the hospital, resulting in increased expense for parents, significantly increased risk for babies and increased profit for the companies. Not only do these efforts send confusing signals to mothers who are simultaneously being encouraged to breastfeed by their health care professionals, but they have also been shown to negatively impact breastfeeding rates.
When they recognized a shift in the medical community towards providing exclusive human milk-based diets for premature infants, Abbott developed a product called “Similac Human Milk Fortifier,” and Mead Johnson developed “Enfamil Human Milk Fortifier.” These names are misleading as it suggests that the products themselves are derived from human milk when in fact, they are cow’s milk-based products. For example, one study found that only 8.8% of parents surveyed in the NICU interpreted “human milk fortifier” as potentially meaning a cow’s milk-based product.

Reasonable Alternative Design
Advances in science long ago created alternative preterm infant formulas and fortifiers that are derived from human milk and non-cow’s milk-based products. In 2006, a company called Prolacta Bioscience introduced a 100% human milk-based fortifier to the U.S. market. Prolacta’s human milk-based fortifier has been continuously sold from 2006 through the present day. In 2014, Prolacta Bioscience began selling a 100% human milk-based ready-to-feed (“RTF”) formula in the United States, which has continuously sold through the present day. Prolacta’s fortifier and formula products contain elements unique to human milk are essential to the growth and development of infants. Further, the use of Prolacta’s formula or fortifier as part of an exclusively human milk-based diet, reduces the odds of NEC in preterm infants by 77% compared to infants who received cow’s milk-based formula or formula fortifiers.
Abbott and Mead Johnson, however, still do not offer any human milk-based products for preterm infants. Thus, despite the existence of reasonable alternative safer products—human milk-based preterm infant nutrition products—Abbott and Mead Johnson continue to specifically market and sell their cow’s milk-based products for preterm infants despite knowing the significant health risk posed to those preterm infants by ingesting these products.
Failure To Warn
Despite their knowledge of the significant health risks posed to preterm infants ingesting their cow’s milk-based products, including the significant risk of NEC and death, Abbott and Mead Johnson do not warn parents or medical providers of the risk of NEC, nor do Abbott and Mead Johnson provide any instructions or guidance on how to properly use their cow’s milk-based products to lower the risk of NEC. In fact, neither of the companies provide any warning in their labeling, websites or marketing that discusses the increased risk of NEC with the use of their cow’s
milk-based products in preterm infants.
Litigation-The Only Way to Promote Change
Unfortunately, given Abbott’s and Mead Johnson’s decision to continue aggressively marketing their cow’s milk-based preterm infant formulas and fortifiers, the only way to ensure they stop marketing these dangerous products for preterm infants is litigation. The injured plaintiffs’ core argument in these cases are straightforward and simple:
- Abbott’s and Mead Johnson’s cow’s milk-based fortifiers and formulas exponentially increase the risk of NEC in preterm infants,
- Abbott and Mead Johnson have known about the increased risk for decades but have failed to warn consumers about the risks, and
- Abbott’s and Mead Johnson’s preterm infant formulas and fortifiers are defectively designed because the companies have failed to remove the cow’s milk proteins from the products despite their clear ability to do so.
Our primary objective is to ensure that the public and the courts are aware of the danger associated with Abbott’s and Mead Johnson’s preterm infant formulas and fortifiers and to ultimately have them taken off the market, especially in light of the existence of safer alternatives that have been available for more than 15 years. Although the legal fight is still in its early stages, the public awareness our efforts are bringing to this issue will ultimately save the lives of thousands of preterm infants. The risk of severe injury and death to preterm infants from these products needs to be widely known and openly discussed, so parents know how to better protect their babies. We are hopeful that our efforts in this fight will result in positive changes for thousands and thousands of families around the world.
Abbott’s And Mead Johnson’s Knowledge of the Risk
Over the past three decades, science and research have confirmed strong links between cow’s milk-based nutrition products and the development of NEC in preterm and severely preterm, low-weight infants. The brand of cow’s milk-based preterm infant nutrition products, whether Similac®, Enfamil® or other makes no difference to the scientific findings. The exact same causative factor exists in both Similac® and Enfamil® preterm infant nutrition products—they are made with cow’s milk rather than human milk. A limited subset of such science/research includes:
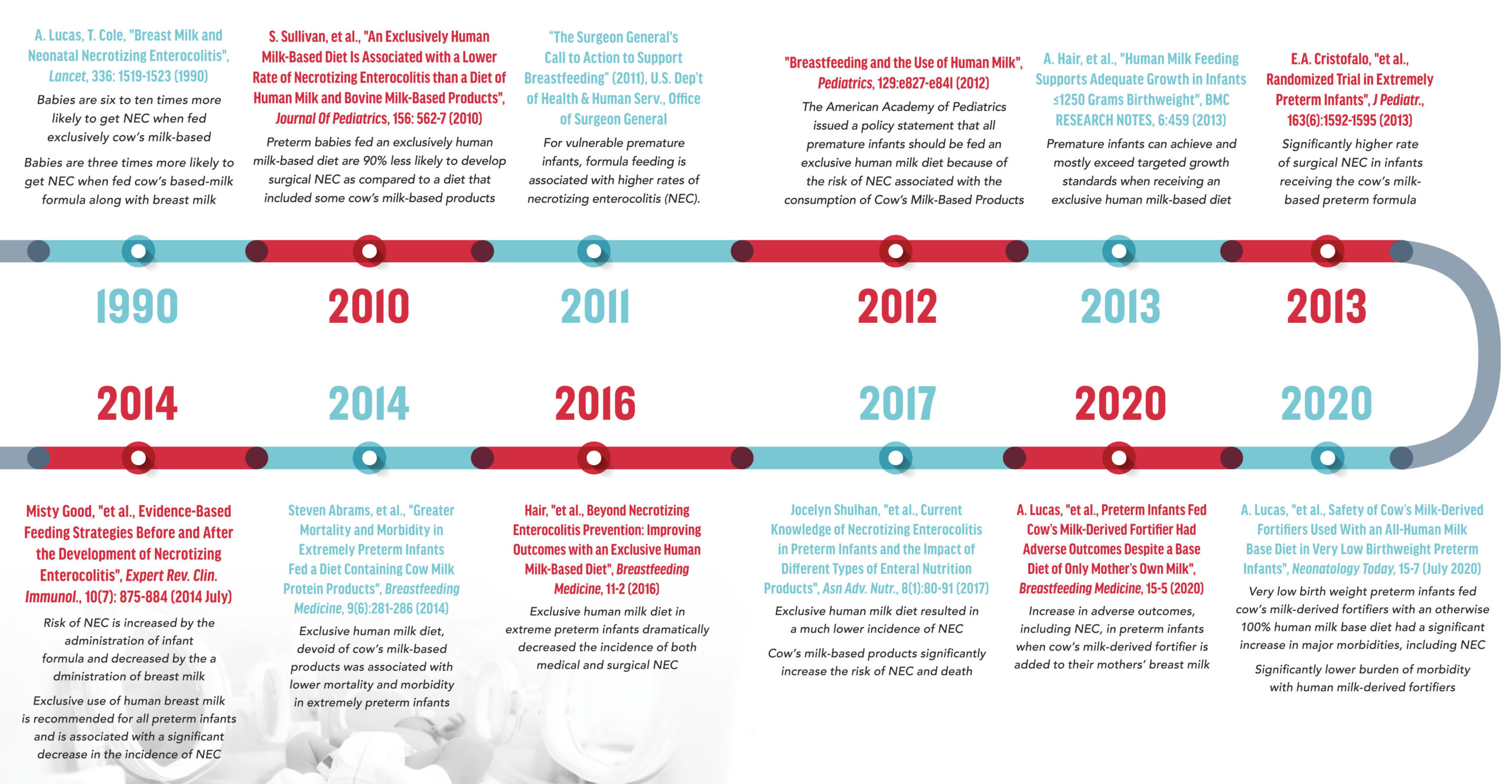
Despite their knowledge and awareness of the above scientific literature, Abbott and Mead Johnson has taken no steps to remove or replace the cow’s milk base of their Similac® and Enfamil® preterm infant nutrition products. Instead, they have continued to produce, market and sell such products specifically for preterm infants, which has resulted in the development of NEC in thousands of preterm infants in the United States.








Leave A Comment